Software in Digital Transformation
 Intro: Accessibility steers every electronic alter
Intro: Accessibility steers every electronic alter
Every significant electronic initiative-cloud movement, crossbreed function, factory-floor telemetry, AI-driven support-hinges on one easy ability: protect, quick accessibility towards the straight body at the correct time. If individuals can not get to the devices as well as information they require, jobs delay, SLAs lapse, as well as your "electronic change" ends up being a move deck rather than a quantifiable result.
Software in Digital Transformation
Unmanaged shortcuts-consumer screen-sharing applications, improvised VPNs, emailed passwords-can relocate a job ahead for a full week as well as collection it rear for a year. Ad-hoc devices produce unseen areas for safety and safety, fragment the individual expertise, as well as make complex audits. The contrary method, a governed remote-access system, compresses onboarding, standardizes manages, as well as provides you observable, repeatable procedures.
Parents of teenager who took his own life sue OpenAI
In the following areas, you will obtain unobstructed meanings for contemporary distant accessibility, useful utilize situations, a 90-day rollout plan, as well as the KPIs that show worth towards leadership-and towards the groups performing the function.
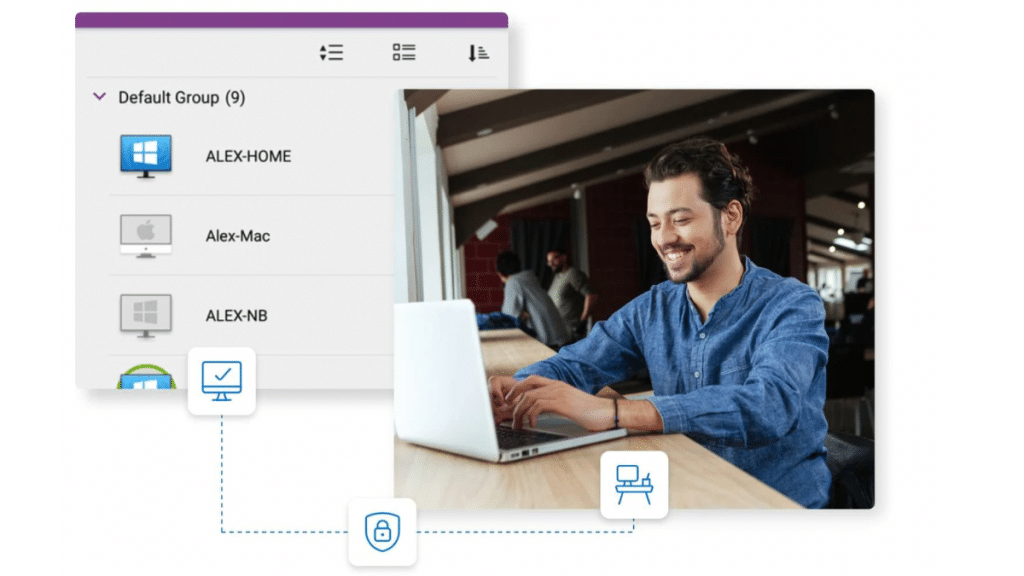
Exactly just what distant accessibility implies in 2025
Distant accessibility is actually no more a basic synonym for "VPN right in to the workplace." In 2025, it is a range:
Gone to vs. ignored accessibility: Gone to treatments link towards an individual that exists (e.g., assist workwork desk sustain). Ignored accessibility gets to gadgets along with nobody at the key-board (e.g., after-hours upkeep on a kiosk or even laboratory PC).
Distant desktop computer vs. push-button control: Distant desktop computer makes the target's complete display; push-button control could be finer-grained ( body, solutions, regulate collection).
Link designs:
Cloud-brokered systems path web website visitor traffic through factors of existence for simple NAT traversal as well as worldwide get to.
Self-hosted entrances maintain web website visitor traffic on facilities you run.
Crossbreed deployments blend each.
Procedures as well as codecs: RDP, VNC, as well as SSH stay staples; contemporary devices include secured relays, GPU-aware streaming, as well as flexible codecs towards protect high top premium at reduced data transfer.
No count on effect: Rather than going down an individual into a level system, no count on licenses a person+device towards a particular application for a particular opportunity home window. The "traditional VPN" ends up being a specific device for restricted situations, certainly not a global door towards whatever.


Komentar
Posting Komentar